Whistleblower Says DOGE Stole Government Data – and Handed It to Russia?
Apr 18 2025A whistleblower at the National Labor Relations Board (NLRB) says that DOGE team members appear to have stolen reams of data from the agency; someone with an IP (Internet protocol) address in Russia simultaneously tried to gain access to the NLRB; and whistleblower, Daniel Berulis, has received threats tacked to his front door.
Mr. Berulis says he’s also heard rumblings from IT employees at other agencies with similar worries that DOGE is secretly exfiltrating sensitive data. And found that another DOGE coder is busy with a product that creates a secret back door into data structures.
Berulis and his attorney, Andrew Bakaj of the nonprofit Whistleblower Aid.
NPR (National Public Radio) broke the story which has been picked up by other news reporting sources but is curiously absent so far from the major newspapers.
The NLRB receives complaints from workers of illegal employer treatment, holds sensitive information on unions, Social Security numbers, home addresses, proprietary corporate data, documentation of ongoing legal cases that contain corporate secrets — Musk's SpaceX among them. Data that…
ENTER DOGE”four labor law experts tell NPR should almost never leave the NLRB and that has nothing to do with making the government more efficient or cutting spending.”
A DOGE team arrived at the NLRB in the first days of March and demanded the highest access level, which gave them unencumbered permission to read, copy, and alter data. In addition, the DOGE team curiously asked that their activities not be logged. All computer system usage by staff at any government agency or corporation of any size is routinely recorded – logged – for security to alert staff to intruders and for troubleshooting should there be system failures. The log enables tracing the path of an intruder’s wanderings through a system. As well, the DOGE crew seemed to try to cover any other tracks by turning off monitoring tools and erasing behind them as they went. These breaches of protocol, Berulis told NPR, were...
"a huge red flag. That's something that you just don't do. It violates every core concept of security and best practice."
No sooner had the Doge team been given full access than came in “near real-time”, according to Berulis, repeated attempts to log into NLRB systems from an IP address – the string of numbers that uniquely identifies a computer — in Russia. The interloper was trying to log into an account just set up by a DOGE team member and even knew the user ID and password. The attempts failed, however, owing to the NLRB’s block against all foreign entry regardless of correct ID and password.
Whether this was a state actor could not be known. Russian hackers are renowned for selling address on the dark Internet, but they in turn might sell their purloined trove to any of a number of our state adversaries – Russia, China, Iran, North Korea.
backdoor manBerulis made another discovery while DOGE was embedded. GitHub is a site (now owned by Microsoft) where developers can create, solely or in collaboration, open source software, meaning creations freely available for use by all. Browsing over a weekend Berulis saw posts on X by MIT graduate and DOGE engineer Jordan Wick about a project he was working on at GitHub that he called "NxGenBdoorExtract."
NxGen is the name of a system at NLRB. "Bdoor" unmistakably alludes to "backdoor", jargon for secret code hidden in a software system that permits illicit entry without user identification or password and known to as few people as only its creator, or in this case suspiciously only DOGE. Perhaps chastised for gabbing in the open, Wick made the posts private, preventing Berulis from probing further. "So when I saw this tool, I immediately panicked, just for lack of a better term", he said.
It looked that DOGE's plan might be to leave behind back doors into data systems throughout the government for Musk and his acolytes, returned to private life, to always be able to hack into government systems and extract data.
warranted search
Once the DOGE engineers left, Berulis tred to put together what pieces he could find to learn what had gone on. In one of his steps, he looked for tracings of data leaving the agency’s various datasets. He saw a chunk of data that had exited NxGen. But then found the motherload — a steep spike leaving the network itself (see screenshot), all of it looking 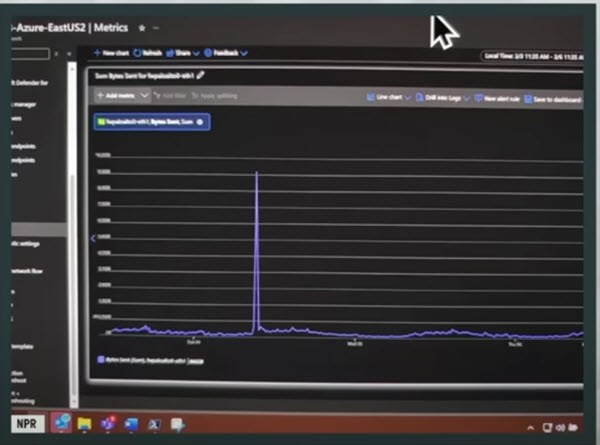
to be text files and totaling some 10 gigabytes. It was not possible to identify any specifics of the data, or whether it had been filtered to extract only files of a sort DOGE might have been looking for, nor could it be ruled out that the data might have been compressed and amount to far more than 10 gigabytes once expanded. In any case, the exfiltration of a vast amount of data was more than unusual because this was data that was never to leave the agency. And, as said, there were no logs to record where the data went.
Berulis and colleagues documented the breach and applied to the Cybersecurity and Infrastructure Security Agency (CISA) for assistance. NPR says, “those efforts were disrupted without an explanation”. At this point, evidently, Berulis decided to go it alone as a whistleblower and submitted an official whistleblower disclosure in a detailed report to Congress and the U.S. Office of Special Counsel. This was subsequently provided to NPR.
threatHe had made the breach known to the NLRB but no further when he went home one night to find a threatening note taped to his front door that contained personal information and an overhead drone photo of him walking his dog. Few knew that address. He had only moved there two months prior and, as he said in an interview, hadn’t yet even reported the address change to his credit card accounts. Clearly it was someone in the NLRB.
vettingNPR says they had Berulis’s report reviewed by 11 technical experts at other government agencies as well as in the private sector, and spoke to over 30 contacts “across the government, the private sector, the labor movement, cybersecurity and law enforcement”.
A knee injury had prevented Berulis from joining the military. He was a volunteer firefighter for a time, then worked for a rape victim hotline, but was a computer savant from an early age and had done work on corporate systems, when the NLRB opportunity opened up. He had immediately set about reinforcing "zero trust" safeguards in the agency's cloud-based data which sees to it that only those who-need-to-know have access, which indicates that Berulis is no ordinary coder.
NLRB was a dream job, he said. "I had an interest in serving my country". Accordingly, Berulis has gone public despite the threat with at least two interviews (PBS NewsHour and Rachel Maddow on MSNBC). He is doing so hopefully to inspire those other IT workers that he had communicated with who had reported suspicious DOGE activity at their agencies.
But with Pam Bondi as attorney general, she who took no action against the reckless incompetence by Defense Secretary Hegseth disclosing in advance on Signal the attack plans against Yemen, it is a safe bet she will not initiate any investigation nor will a Republican-controlled Congress terrified of Trump.
Please subscribe if you haven't, or post a comment below about this article, or
click here to go to our front page.

